Table of Contents
Introduction– Virus Alert
In an era dominated by digital interactions, the shadow of cyber threats looms larger than ever before. Among these, the insidious spread of fake virus notifications has emerged as a formidable menace, preying on the unsuspecting and sowing seeds of panic. These deceptive alerts, often masquerading as urgent system warnings or alarming virus detections, have the potential to wreak havoc on personal devices and compromise sensitive data. Understanding the tactics behind these fake notifications is crucial in safeguarding oneself against their cunning ploys.
The Rise of Deceptive Virus Alerts: Unmasking the Threat
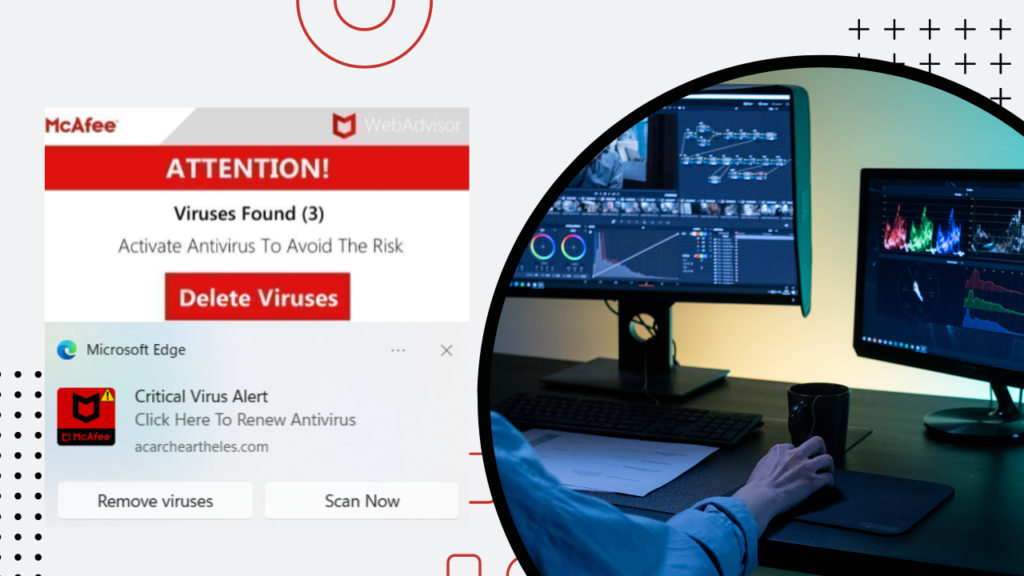
In recent times, the digital landscape has witnessed a concerning surge in fake virus notifications. These deceptive messages are engineered to trigger immediate panic, exploiting the common fear of data loss and system compromise. By mimicking the appearance of legitimate antivirus alerts or official system messages, cybercriminals aim to create an atmosphere of urgency, forcing users into impulsive actions. Such notifications infiltrate various digital realms, from web browsers to emails and even mobile apps, leaving users vulnerable to their trickery.
Example: John, a diligent professional, was startled when a pop-up on his browser warned him of a severe virus outbreak on his system. The notification demanded immediate action, urging him to click on a link for a “quick fix.” Panicked, he complied, only to realize later that he had fallen victim to a fake virus notification, inadvertently downloading malware onto his system.
Staying Vigilant in a Digital Minefield
Amidst this onslaught of deceptive alerts, the paramount importance of remaining vigilant and informed cannot be overstated. Users must develop a keen eye for detecting the subtle differences between genuine and fake virus notifications. Genuine alerts often carry a professional tone, concise language, and come from recognized sources such as established antivirus software or operating systems. On the other hand, fake notifications tend to be riddled with spelling errors, use generic language, and prompt users to take immediate, unplanned actions.
Key Points:
- Genuine alerts exhibit professionalism and clarity in their messages.
- Legitimate notifications usually come from well-known sources like reputable antivirus programs.
- Fake alerts often contain grammar and spelling mistakes and employ scare tactics to coerce users into action.
Understanding Fake Virus Alert
In the digital realm’s labyrinth of threats, fake virus notifications stand as cunning adversaries, exploiting both technology and human psychology. These deceptive alerts mimic legitimate warnings and exploit users’ fears to extract compliance, often leading to disastrous outcomes.
Defining Fake Virus Notifications and Their Operations
Fake virus notifications are crafted by cybercriminals to resemble authentic alerts from antivirus software or operating systems. Their primary objective is to manipulate users into believing that their devices are infected with malware or viruses. Once a user interacts with these notifications, the perpetrators aim to achieve various malicious goals, including spreading malware, stealing personal information, or initiating financial scams.
These notifications typically masquerade as urgent system warnings, offering a “quick fix” by prompting users to click on a link, download a file, or provide sensitive information. By capitalizing on users’ fears of data loss and system compromise, cybercriminals aim to exploit their impulsiveness, tricking them into taking actions that serve the perpetrators’ interests.
Common Platforms for Encountering Fake Virus Alert
Fake virus notifications cast a wide net across various digital platforms, exploiting vulnerabilities in common environments where users are likely to encounter them:
- Browsers: Cybercriminals design fake alerts to appear as pop-ups within web browsers, often triggered by visiting compromised or malicious websites. These pop-ups warn users of detected viruses and encourage them to take immediate action, which usually involves clicking on a link or downloading a supposed “security tool.”
- Emails: Emails containing fake virus alerts can land in users’ inboxes, appearing to originate from reputable sources like antivirus companies or tech support. These emails may contain alarming subject lines and urge recipients to open attachments or click on links that lead to malicious websites.
- Pop-ups: Fake virus notifications can manifest as pop-ups while users navigate websites or interact with online content. These pop-ups might mimic system alerts, informing users of detected malware and coercing them to click for a resolution.
Psychological Tactics: Instilling Panic for Compliance
The success of fake virus notifications lies in their ability to exploit human psychology, triggering panic and urgency to manipulate users into hasty actions. Perpetrators deploy several psychological tactics to achieve their goals:
- Fear and Urgency: Fake alerts play on users’ fears of data loss, financial harm, or identity theft. The urgent language and dire consequences described in these notifications amplify the sense of impending doom, leaving users desperate to take immediate action.
- Authority Impersonation: By mimicking the appearance of legitimate antivirus software or official system messages, fake notifications exploit users’ trust in recognized brands and systems, making them more likely to comply with the notification’s demands.
- Isolation and Panic: Cybercriminals create a sense of isolation, making users believe that their devices are severely compromised. This isolation fuels panic and inhibits users from seeking help from reliable sources, pushing them to act impulsively.
In this treacherous landscape of digital deception, understanding these tactics is the first step toward protecting oneself from falling victim to fake virus notifications. Armed with knowledge, users can navigate the digital realm with confidence, distinguishing genuine alerts from deceptive traps.
The Threats of Fake Virus Notifications
The alluring facade of fake virus notifications conceals a multitude of dangers that can wreak havoc on both personal devices and the lives of unsuspecting users. Interacting with these notifications opens the door to a realm of malicious possibilities, ranging from data compromise to financial ruin.
Consequences of Interacting with Fake Virus Notifications
- Malware Installation: Clicking on links or downloading files from fake notifications can lead to the inadvertent installation of malware. This malicious software can include viruses, spyware, ransomware, and keyloggers, compromising system security and potentially rendering devices unusable.
- Data Theft and Privacy Breach: Cybercriminals often design fake alerts to extract sensitive information, such as login credentials, financial data, or personal details. Users who unknowingly provide this information become vulnerable to identity theft, unauthorized financial transactions, and further cyberattacks.
- Financial Scams: Fake virus notifications can be a gateway to financial scams. Perpetrators may ask users to pay for unnecessary and often ineffective “security solutions.” Alternatively, they might employ scare tactics, coercing victims into sharing credit card information or making unauthorized payments.
Real-World Examples of Fake Alert Incidents
- Tech Support Scams: In one notorious case, victims received a pop-up notification claiming their systems were infected. The notification provided a toll-free number for “tech support.” Upon calling, victims were manipulated into granting remote access to their devices and paying exorbitant fees for nonexistent services.
- Ransomware Attacks: Fake notifications can sometimes initiate ransomware attacks, where victims’ data is encrypted and held hostage until a ransom is paid. Such attacks have crippled businesses and individuals alike, causing financial losses and data breaches.
- Email Phishing: Fake virus notifications sent via email can lead to phishing attacks. Victims may click on malicious links or download infected attachments, unwittingly compromising their systems and falling victim to subsequent cybercrimes.
Example: Jane, a college student, received a fake virus notification claiming her laptop was compromised. The notification urged her to download a “security tool” from a link. Trusting the urgency of the message, Jane complied. Unbeknownst to her, the tool contained malware that harvested her sensitive data, leading to unauthorized credit card transactions and identity theft.
The tales of these incidents underscore the sinister impact of fake virus notifications. Whether it’s a devastating malware infection or a financial scam that drains victims’ resources, the risks are both tangible and far-reaching. To shield themselves from these dangers, users must arm themselves with knowledge and adopt a cautious approach when confronted with unsolicited alerts.
Identifying Fake Virus Notifications
Amid the sea of digital notifications, the ability to distinguish genuine alerts from their deceptive counterparts is paramount. By honing in on specific characteristics, users can fortify their defenses against the sly tactics of fake virus notifications.
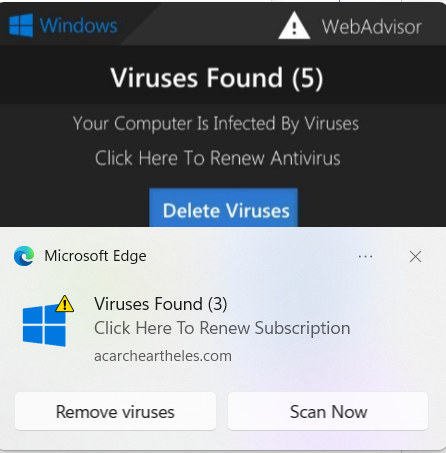
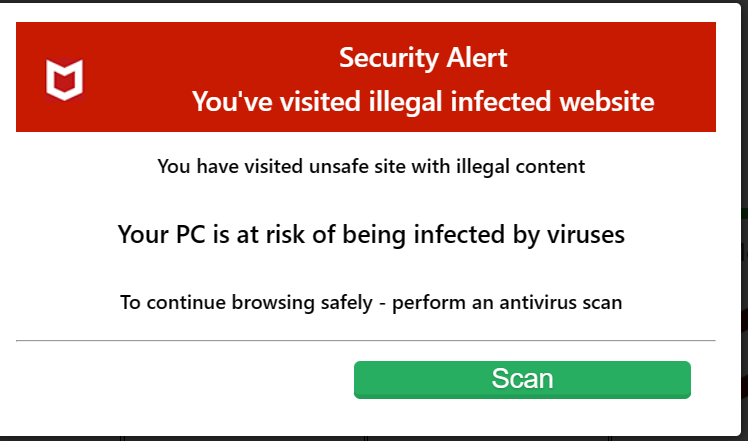
Characteristics of Genuine vs. Fake Virus Notifications
- Professional Language and Tone: Legitimate alerts exhibit a professional and concise language, devoid of exaggerated claims or aggressive urgency. Fake notifications, on the other hand, often employ alarming language designed to induce panic and coerce swift action.
- Recognizable Branding: Trusted antivirus software or operating systems use consistent branding and design elements in their notifications. Genuine alerts come from recognized sources and carry the credibility of these established brands.
- Detailed Information: Authentic notifications provide specific details about the detected threat, including the type of virus or malware and its potential impact. Fake notifications tend to be vague, emphasizing fear rather than information.
Detecting Red Flags: Grammar, Spelling, and Language
- Grammar and Spelling Errors: Fake virus notifications frequently contain grammar and spelling mistakes. These errors are a clear indication of a lack of professionalism, as reputable companies ensure their communications are error-free.
- Generic Language: Fake alerts often use generic phrases that lack personalized information. Legitimate notifications address users by their names and offer context relevant to their devices or operating systems.
- Urgent Demands: Phrases like “Your system is compromised!” or “Act now to prevent data loss!” are common in fake notifications. Such sensational language is intended to elicit immediate reactions without thoughtful consideration.
Tracing Suspicion: Suspicious Sender Addresses
- Email Addresses: Examine the sender’s email address closely. Fake notifications may use email addresses that resemble official ones but contain slight variations or misspellings.
- Domain Verification: Legitimate notifications are sent from official domains associated with reputable antivirus companies or operating systems. Verify the domain in the email address to confirm its authenticity.
Seeking Trustworthy Sources: Official Virus Notifications
- Antivirus Software: Reputable antivirus software providers, such as McAfee, Norton, or Bitdefender, issue legitimate alerts regarding virus detections. However, be cautious of pop-ups from unknown sources claiming to be antivirus providers.
- Operating Systems: Operating system developers, like Microsoft or Apple, communicate through official channels for system-related notifications. These notifications should never ask users to provide personal information or download files.
- Security Center or Settings: For added assurance, access the security center or settings of your device directly. Legitimate notifications are often accompanied by matching alerts in these settings.
In the digital age, where deceptive schemes abound, identifying fake virus notifications is a vital skill. By scrutinizing language, sender addresses, and the legitimacy of the source, users can equip themselves to navigate the labyrinth of notifications with discernment. In the pursuit of digital security, the ability to separate fact from fiction stands as a formidable shield against cyber threats.
Step-by-Step Guide to Removing Fake Virus Alert
1.Stay calm and Do Not Interact
In the face of a potentially alarming situation like encountering a fake virus notification, maintaining your calm and adopting a composed approach is pivotal. Hasty actions driven by panic can inadvertently open the door to cyber threats. Here’s how you can effectively navigate such scenarios while keeping a level head.
Advise Against Clicking Links or Buttons
Beware the Temptation of Immediate Clicks
When faced with a notification claiming urgency, the urge to click on provided links or buttons might be strong. However, clicking on these elements within a fake virus notification could lead you down a perilous path. Cybercriminals often design these links to install malware, initiate phishing attacks, or direct you to malicious websites. Avoid the temptation to click without first validating the authenticity of the notification.
Encourage Avoidance of Phone Calls
Doubtful Numbers: A Red Flag
Some fake virus notifications include phone numbers under the guise of offering technical support. However, dialing these numbers can expose you to potential scams. Cybercriminals behind these notifications might pose as tech support agents, aiming to manipulate your fears and extract personal information or gain remote access to your device. Instead of calling these numbers, seek assistance from reputable sources independently.
Highlighting the Perils of Panic-Driven Decisions
The Pitfalls of Panic
Panic often clouds rational thinking and impels us to make hasty decisions. Fake virus notifications are designed to evoke fear and urgency, exploiting these emotions to coerce immediate action. However, giving in to panic can lead to unintended consequences. Engaging with the notification without careful consideration can result in compromised security, loss of personal data, and exposure to financial risks.
Example Scenario:
Paragraph: Imagine receiving a pop-up notification claiming your computer is infected with a dangerous virus that threatens your personal files. Your heart races, and panic sets in. In this scenario, it’s easy to fall into the trap of hastily clicking on the “Fix Now” button out of fear. However, taking a moment to breathe and assess the situation critically can save you from potential harm. Instead of clicking, you decide to close the notification and conduct your research. This decision shields you from a potentially malicious link and gives you the time needed to seek guidance from reliable sources.
In the digital realm, staying calm is your armor against the tactics of cybercriminals. By resisting the impulse to click, avoiding dubious phone numbers, and recognizing the perils of panic, you empower yourself to make informed choices that safeguard your digital well-being.
2. Close the Browser Tab or Window
Encountering a suspicious notification can be unnerving, but taking swift action to close the browser tab or window is a crucial step in preventing any potential harm from fake virus alerts. Here’s how to ensure a prompt response and protect your digital environment.
Using the “X” Button or Keyboard Shortcut
When faced with a pop-up notification that raises doubts or concerns, your first line of defense is to immediately close the tab or window containing the alert. Here’s how you can do it:
- Click the “X” Button: Look for the small “X” icon usually located at the top right corner of the browser tab. Clicking this button will instantly close the tab and terminate the notification.
- Keyboard Shortcut (Ctrl+W or Command+W): Alternatively, you can use the keyboard shortcut Ctrl+W (Windows) or Command+W (Mac) to swiftly close the active tab. This shortcut is a quick and efficient way to eliminate the threat without further interaction.
Dealing with Unresponsive Browsers
In some cases, the browser might become unresponsive due to the notification or the associated content. If attempting to close the tab or window doesn’t work, don’t panic. Here’s what you can do:
- Access Task Manager (Ctrl+Shift+Esc): On Windows, pressing Ctrl+Shift+Esc simultaneously will open the Task Manager. On Mac, you can use the Activity Monitor. Identify the unresponsive browser process from the list and choose to end it. This action will force-close the browser and terminate any potentially malicious processes.
Remember, closing the browser tab or window promptly is a proactive step that prevents further interaction with the fake virus notification. By using the provided methods, you ensure that you swiftly disconnect from the potential threat and regain control of your online experience.
3.Clear Browser Cache and Cookies
Clearing your browser’s cache and cookies is a crucial step after encountering a suspicious notification. This process helps remove stored data that could potentially be linked to the fake virus notification and ensures a cleaner online environment. Follow these step-by-step instructions to navigate your browser settings and clear browsing data effectively.
Finding Your Browser Settings
- Open Your Browser: Launch your preferred web browser (e.g., Google Chrome, Mozilla Firefox, Microsoft Edge, Safari).
- Access Settings: Look for the three vertical dots (Chrome), three horizontal lines (Firefox), or the gear icon (Edge) usually located in the upper-right corner of the browser window. Click on it to open the browser menu.
Clearing Browsing Data
Navigate to Clear Browsing Data
- Chrome: From the browser menu, hover over “More tools,” then select “Clear browsing data.”
- Firefox: Click on “Options,” then choose “Privacy & Security” from the left sidebar. Under “Cookies and Site Data,” click on “Clear Data.”
- Edge: Click on “Settings,” then select “Privacy, search, and services.” Under “Clear browsing data,” click on “Choose what to clear.”
Step Instructions for Clearing Data
Select the Data to Clear
- Choose Time Range: In most browsers, you’ll have the option to choose the time range for which you want to clear data. Select “All time” to ensure a thorough cleaning.
- Select Data Types: Check the boxes next to “Cookies and other site data” and “Cached images and files.” These are the key elements that could potentially be linked to the fake notification.
Emphasizing the Importance of Selection
Why Clear Cookies and Cached Images?
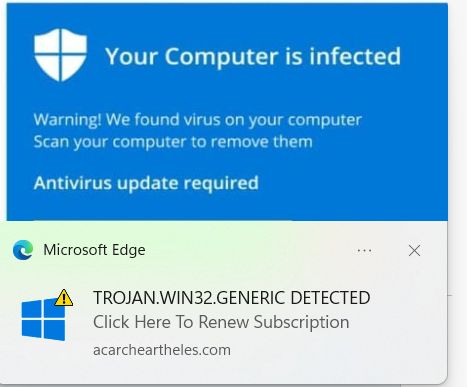
- Cookies: Clearing cookies removes small files stored on your device that track your online activities. Fake notifications might have used cookies to track your interaction, and clearing them enhances your privacy and security.
- Cached Images and Files: Cached data helps websites load faster, but it can also store elements from the fake notification. Clearing cached images and files ensures that any potentially compromised content is removed.
Example Scenario:
After encountering a suspicious notification while browsing, you decide to take action. Opening the browser settings, you find the “Clear browsing data” option and select it. Opting for the “All time” range, you ensure a thorough cleanup. Understanding the significance of cookies and cached images, you diligently check the boxes next to “Cookies and other site data” and “Cached images and files.” With a click, you initiate the process, removing any traces of the fake notification from your browsing history and data storage.
Clearing your browser cache and cookies acts as a digital reset, eliminating potential connections to deceptive notifications. By following these instructions, you proactively protect your online security and privacy, ensuring a safer browsing experience moving forward.
4.Run a Legitimate Anti-Malware Scan
When facing the aftermath of encountering a fake virus notification, running a thorough anti-malware scan is a crucial step to ensure the safety of your system. Here’s how you can effectively utilize reputable antivirus or anti-malware software to safeguard your digital environment.
Using Reputable Antivirus or Anti-Malware Software
Choose Trustworthy Protection
- Select a Reliable Software: Ensure you have reputable antivirus or anti-malware software installed on your device. Choose software from well-known companies with a proven track record in cybersecurity.
- Update Software: Before initiating a scan, make sure your antivirus software is up to date. Regular updates ensure your software is equipped to detect the latest threats.
Initiating a Full System Scan
Scanning for Comprehensive Security
- Open Antivirus Software: Launch your antivirus or anti-malware software from your desktop or system tray.
- Choose Full Scan: Look for an option labeled “Full Scan” or “Complete Scan.” This type of scan examines your entire system, including all files and folders.
- Start the Scan: Click on the “Start” or “Scan” button to initiate the full system scan. The software will systematically inspect your files and directories for potential threats.
Quarantining or Removing Detected Threats
Handling Identified Threats
- Review Scan Results: Once the scan is complete, your antivirus software will display the results. It will identify any potential threats found during the scan.
- Quarantine or Remove: Depending on the severity of the threats, your software might provide options to quarantine or remove the detected files. Quarantining isolates the files from the rest of your system, while removal deletes them entirely.
- Follow Recommendations: Trust the expertise of your antivirus software. If it recommends quarantine or removal, follow those suggestions to neutralize potential threats effectively.
Example Scenario:
Faced with the aftermath of a fake virus notification, you decide to employ your trusted antivirus software for a comprehensive system scan. Ensuring that your software is updated, you launch it and select the “Full Scan” option. With a click, the scan begins, thoroughly inspecting every corner of your device for any malicious entities. After completion, you review the results, where the software identifies a few potentially harmful files. Trusting the software’s expertise, you choose to quarantine the files, preventing them from causing any further harm to your system.
Running a legitimate anti-malware scan is akin to enlisting a digital guardian to cleanse your device of potential threats. By adhering to these steps and using reputable software, you bolster your system’s defenses and ensure a safer online experience.
5.Update Operating System and Software
Maintaining the security of your digital ecosystem hinges on a fundamental principle: keeping your operating system and software up to date. Neglecting updates can expose vulnerabilities that cybercriminals exploit. Here’s how you can proactively ensure your digital environment remains fortified.

The Significance of Regular Updates
Building a Shield of Vigilance
- Security Patches: Software updates often include critical security patches that address vulnerabilities. Failing to update leaves these vulnerabilities open, allowing cybercriminals to exploit them.
- Enhanced Features: Beyond security, updates offer improved features, performance optimizations, and compatibility enhancements. Regular updates guarantee a seamless and secure digital experience.
Instructions for Updating Operating Systems, Browsers, and Security Software
Nurturing Digital Hygiene
- Operating Systems:
- Windows: Click on the “Start” button, go to “Settings,” select “Update & Security,” and click “Check for updates.”
- Mac: Click on the Apple menu, choose “System Preferences,” and select “Software Update” to check for and install updates.
- Browsers:
- Chrome: Click the three vertical dots, select “Help,” then click “About Google Chrome” to trigger automatic updates.
- Firefox: Click the three horizontal lines, choose “Options,” select “General,” and scroll down to “Firefox Updates” to enable automatic updates.
- Edge: Updates are automatically delivered through Windows Update.
- Security Software:
- Open your antivirus or anti-malware software.
- Look for an option related to updates or settings.
- Enable automatic updates to ensure your software is always current.
6.Educate Others
Spreading the Shield of Knowledge
- Share Experiences: If you’ve encountered fake virus notifications or other cyber threats, share your experiences with friends and family. Sharing real-life stories fosters awareness and encourages vigilance.
- Emphasize Awareness: Cyber threats thrive in an environment of ignorance. Remind your loved ones that being aware of digital risks is the first step in preventing them. Encourage them to stay informed about the latest cybersecurity trends.
Example Scenario:
Paragraph: Armed with the knowledge of the importance of updates, you decide to take charge of your digital security. You follow the instructions to update your operating system, browsers, and security software, ensuring that no vulnerabilities remain unaddressed. The process is seamless and reassuring, knowing that your efforts contribute to a robust digital defense. Inspired by your newfound awareness, you share your experience with your family over dinner. As you discuss the significance of updates and cybersecurity, you notice a newfound sense of caution and curiosity among your loved ones.
In the realm of digital security, knowledge is power. By heeding the call to keep your software updated and by sharing your experiences with others, you cultivate a community of informed and resilient users. Your actions not only protect your own digital environment but contribute to the collective strength against cyber threats.
Preventing Future Fake Virus Notifications
Protecting yourself from the clutches of fake virus notifications requires a proactive stance and a commitment to digital hygiene. By following these measures, you can fortify your defenses against deceptive threats.
Minimize Risk with Proactive Steps
Building Digital Fortifications
- Verify Sources: Always verify the legitimacy of alerts. Only trust notifications from recognized antivirus software, operating systems, or trusted sources.
- Enable Pop-Up Blockers: Adjust your browser settings to block pop-ups. This simple step can prevent intrusive fake notifications from even reaching your screen.
- Stay Educated: Stay informed about the tactics cybercriminals use. Knowledge is your armor against their strategies.
Advocating Browser Extensions
Guarding Against Intrusion
- Install Ad Blockers: Browser extensions that block ads and pop-ups offer an added layer of defense against intrusive notifications.
- Malicious Content Filters: Extensions that filter malicious content safeguard your online experience from potential threats.
Promoting Secure Browsing Habits
Navigating the Digital Landscape Wisely
- Beware of Unknown Links: Refrain from clicking on links from unverified sources, especially if they arrive through emails or unfamiliar websites.
- Check URLs: Scrutinize URLs for authenticity before entering personal information or clicking on any links. Secure websites often start with “https://.”
Conclusion
In the intricate tapestry of the digital world, staying informed and cautious is paramount. The prevalence of fake virus notifications serves as a reminder that our vigilance must be unwavering.
Recapping Vigilance and Awareness
By remaining vigilant, you shield yourself from the intricate webs woven by cybercriminals. Recognizing the signs of fake virus notifications and staying abreast of emerging threats will keep you one step ahead.
Empowering Action
If confronted with a fake virus notification, remember to stay calm, not interact with the notification, and follow the steps outlined to secure your device. By taking control of your online security, you empower yourself to navigate the digital landscape confidently.
Spreading Knowledge
Share your newfound knowledge with friends, family, and anyone who navigates the digital realm. In a world where cybersecurity is paramount, your role as an advocate for informed digital practices is pivotal.
In a realm where digital threats continually evolve, your commitment to vigilance and knowledge transforms you into a guardian of your own digital domain. The keys to security lie within your grasp, as you harness the power of understanding and caution to build a safer online world for yourself and those around you.